Best Practices for Secure Email Attachments Downloads
In our increasingly connected world, email remains a vital communication tool for both personal and professional use. However, the convenience of email also brings significant security risks, especially when it comes to downloading and managing attachments.
This article will explore essential practices for securing email communications, focusing on safe file downloads, the role of antivirus scanners, the implications of automatic downloads, and the critical importance of email and file encryption.

Understanding Email Viruses
Email viruses are malicious software programs distributed through email messages. They can be attached to emails as files, embedded within the email's content, or disguised as links. When recipients interact with these attachments or links, the virus activates and can infect their computer systems. Here are some of the most common types:
Phishing Emails
These emails come from legitimate sources (banks, social media platforms, etc.) and often contain malicious attachments or links. The attachment or link, when opened, installs malware on the victim's computer.
Trojan Horse Attachments
These emails contain attachments that, when opened, install Trojan horse malware on the victim's system. Trojans can create backdoors for hackers to access the system, steal data, or use the infected machine for other malicious activities.
Worms
When the attachment is opened, the worm installs itself on the victim's computer and then uses the victim’s email contacts to send copies of itself.
Safe Practices for Email File Downloads
Downloading files from emails is a common practice, but it can expose users to potential threats if not managed carefully. Cyber threats such as malware, phishing attempts, and data breaches are ever-present, making the security of email files a top priority.
Be Cautious with Email Attachments and Links
Check the sender's email address carefully and do not open files (.exe, .scr) and script files (.js, .vbs). These file types pose higher risks and should be avoided unless trustworthy. Even if the email appears to come from someone you know, verify if the attachment was expected. The sender may not know that the email was sent from their address.
In addition to email attachments, watch out for links within the text. Hover over links to see the actual URL before clicking and avoid clicking on links that seem suspicious or unfamiliar.
Use Reliable Antivirus Software
Reliable antivirus software is a critical defense layer, detecting and removing malware, preventing the spread of infections, and safeguarding against data theft and financial loss.
Make sure your antivirus software is set to scan the system regularly. Also enable real-time protection to detect and block threats as they occur. And don't forget to keep your antivirus software and its virus definitions up to date to detect the latest threats.
Enable Email Filtering
Email filtering is the process of automatically sorting and managing incoming and outgoing emails based on predefined criteria. These criteria can include sender information, email content, attachments, and other factors. Use spam filters to block unwanted and potentially harmful emails.
Use Strong, Unique Passwords
The best practice is using a password manager to generate and store strong, unique passwords for each account, significantly reducing the risk of password cracking. Password managers typically autofill passwords only on the correct websites, helping to protect against phishing attacks that attempt to trick you into entering your credentials on fake sites.
Implement Email Security Solutions
Use end-to-end encryption where possible, ensuring that only the sender and recipient have the keys to decrypt the message. Other security measures include implementing DMARC policies to protect your email domain from being exploited for phishing and spoofing attacks.
Educate Yourself
Regularly educating yourself and others about the latest cybercriminal scams is one of the important pillars of security. You can use online forums or attend security courses and lectures to educate yourself.
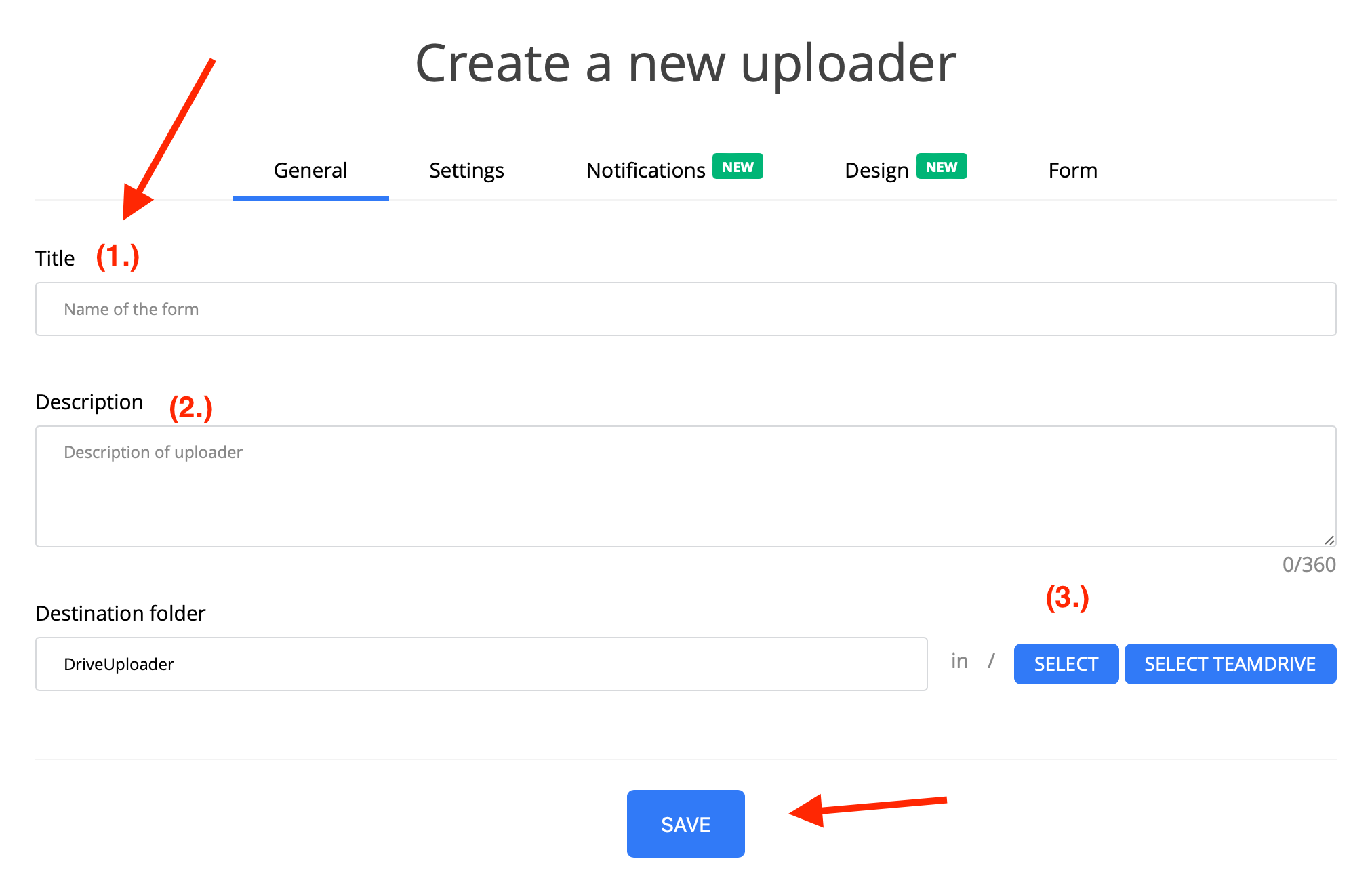
Safe downloading of email attachments
Protect your computer from potential threats by storing email attachments directly in the cloud. Proven online storages like Google Drive have automatic file scanning that can protect all your data from a potential attack. However, how do I get my email attachments stored directly on Google Drive?
If you use Gmail, you can download an email attachment to your Google Drive by clicking on the "Organize in Drive" option that appears when you hover over the file. However, if you prefer a different email client or are looking for more features, we recommend choosing a third-party application to store email attachments in your cloud.
Quick recap
Email is an indispensable tool, but its usage comes with inherent security risks. By adopting safe download practices, utilizing robust antivirus solutions, employing strong encryption, and using secure automatic email attachment downloading services like DriveUploader, both individuals and organizations can significantly enhance their email security. Staying informed and vigilant is the best defense against the ever-evolving landscape of email-based threats.